Cloud protection strategies against dangling IP takeovers

Cloud computing has revolutionised business operations, but it also introduces new security challenges. One such challenge is the risk of dangling IP takeovers, a vulnerability that attackers can exploit to intercept traffic and conduct malicious activities. This article explains the nature of dangling IPs, their security implications, and strategies to mitigate this risk.
IP address takeovers
There are two types of IPs relevant to this discussion:
- Elastic IPs (EIPs): These are static IPv4 addresses provided by cloud service providers like AWS. EIPs can be associated with any instance in a user's account and reassigned as needed. An EIP becomes "dangling" in two main scenarios: firstly, if it is disassociated from an instance but not returned to the IP address pool, it is considered dangling because it is no longer in active use but still allocated to the account. An EIP can also become dangling when it is released back to the pool, but a DNS record continues to point to it.
- Ephemeral IPs: These are temporary public IPs assigned to instances when they are launched. If an instance is stopped or terminated, the ephemeral IP is released back to the pool. However, if a DNS record points to this now-released IP, it becomes a dangling reference, vulnerable to takeover.
The distinction between elastic and ephemeral IPs is crucial in understanding the risk landscape and implementing appropriate security measures.
The threat landscape
Dangling IPs pose significant security risks. Attackers can exploit these vulnerabilities to launch phishing campaigns, distribute malware, or steal sensitive data. Given the inherent trust in cloud services, users might not suspect the malicious use of these IPs, making them an effective vector for cyber-attacks. The repercussions for organisations include not only reputational damage but also regulatory penalties and substantial financial losses, highlighting the critical need for robust security measures.
Potential exploits by attackers
Exploiting Dangling Elastic IPs
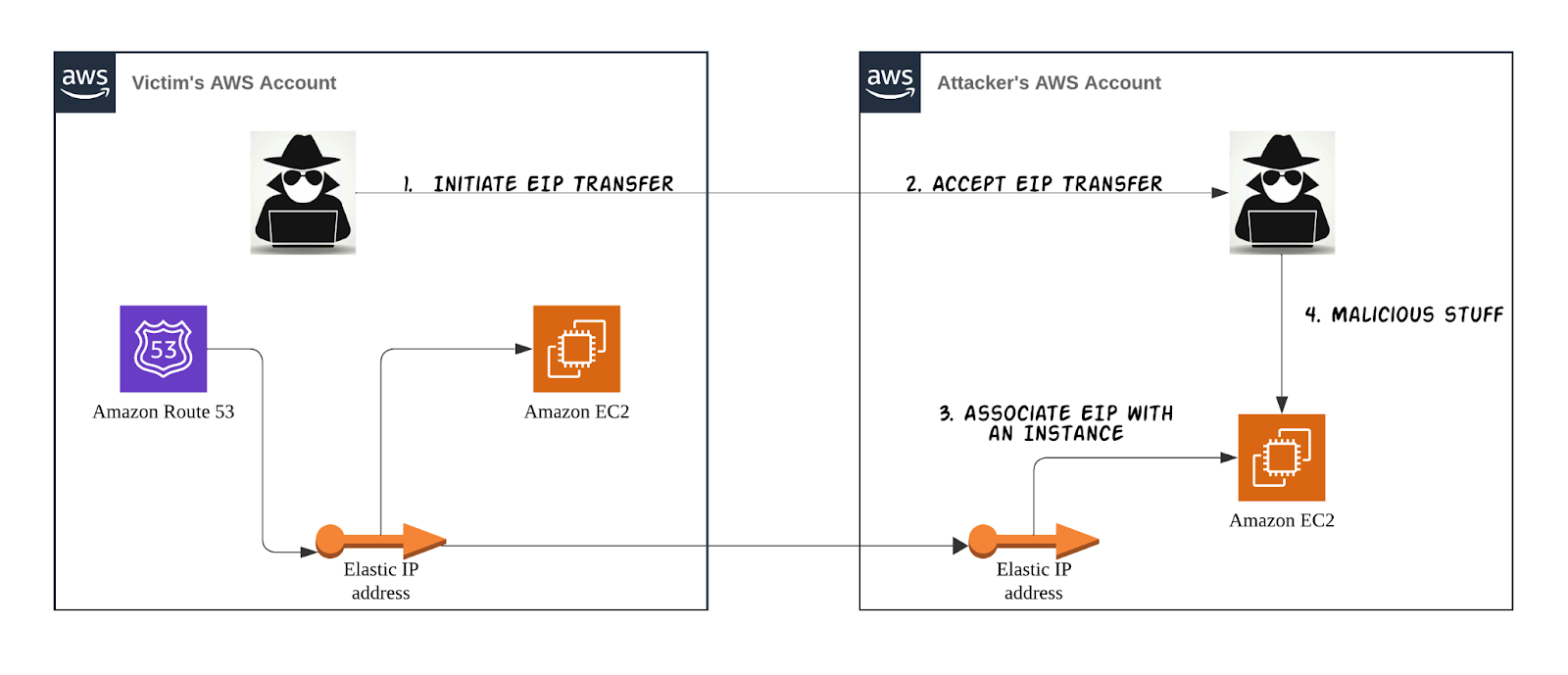
An attacker’s exploitation of a dangling Elastic IP typically involves several steps and requires specific conditions to be met:
- Discovery of vulnerability: The attacker begins by identifying a dangling EIP. This identification can result from reconnaissance or accidental discovery.
- Gaining account access: To move forward, the attacker must gain some level of access to the target AWS account holding the dangling EIP. This could involve compromising account credentials, exploiting overly permissive Identity and Access Management (IAM) roles, or finding other security vulnerabilities that provide an entry point into the account.
- EIP transfer request: With access to the account, the attacker can request for the EIP to be transferred to their own AWS account. This step is crucial as it requires the attacker to manipulate cloud service configurations to redirect the EIP away from its legitimate owner.
- Malicious activities: Once the transfer is successful, the attacker associates the now-controlled dangling EIP with an instance in their possession. This control allows them to intercept, manipulate traffic, or launch a variety of cyber-attacks ranging from data breaches to distributing malware, leveraging the trusted reputation of the services associated originally.
Exploiting dangling ephemeral IPs
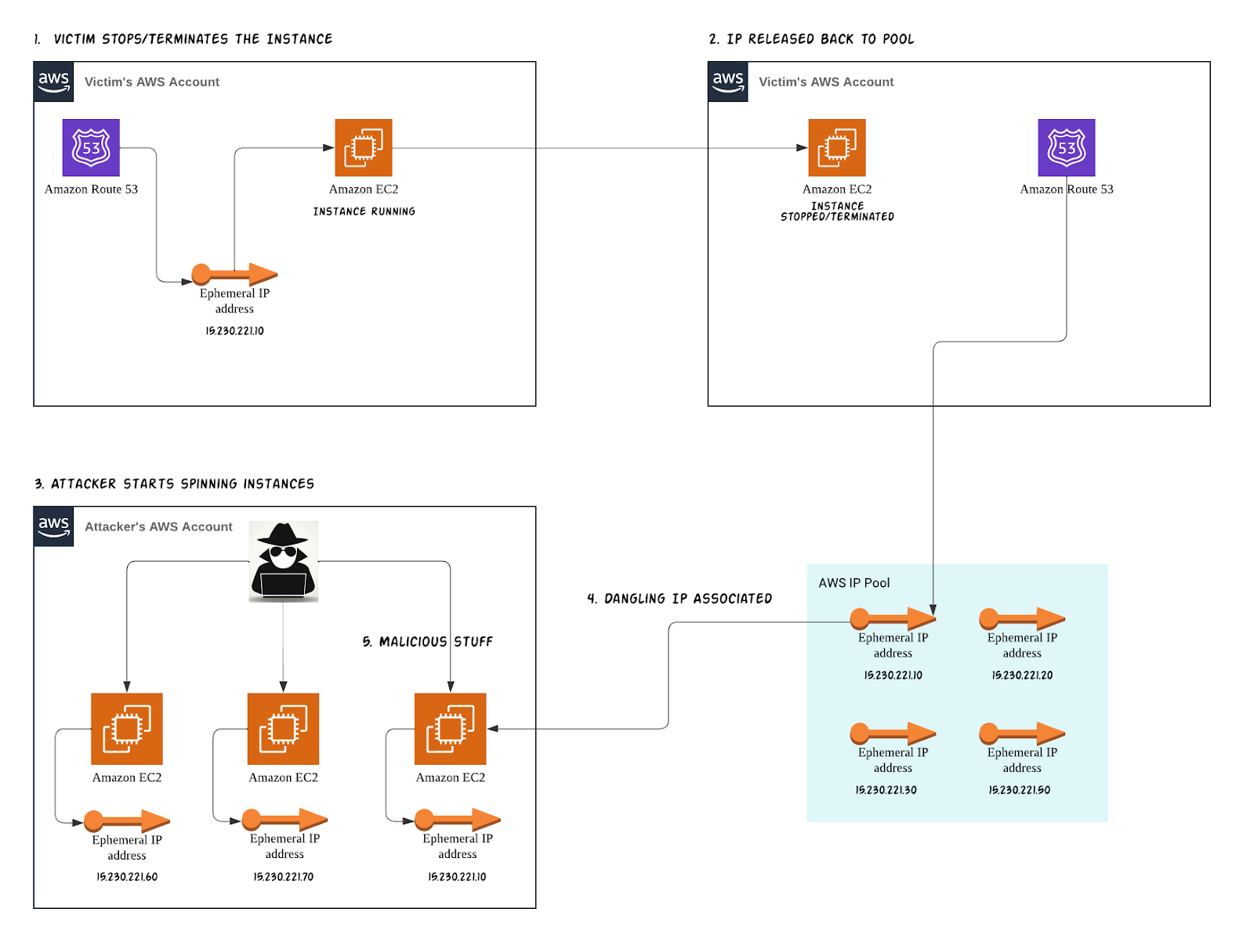
The exploitation of dangling ephemeral IPs presents a relatively straightforward process compared to their elastic counterparts, primarily because the attacker doesn’t need access to the victim's cloud accounts. Here is how attackers might use these vulnerabilities:
- Identification of vulnerability: Attackers discover that an ephemeral IP has been left dangling. This could be achieved through targeted reconnaissance or by chance.
- Instance launching attempt: They then launch new instances in their cloud account, hoping to be assigned the identified dangling IP by the cloud's IP allocation system.
- Exploitation: Successful acquisition allows the attacker to intercept and manipulate the traffic intended for the original service. The attacker can now initiate a variety of malicious activities. These activities might range from intercepting and manipulating traffic meant for the original service to launching phishing campaigns or distributing malware.
Similarly, Dangling Elastic IPs are vulnerable to exploitation when they become disassociated from instances and are returned to the pool. In such cases, attackers can start acquiring and releasing Elastic IPs until they get the one they need.
Strategies for mitigating risks of dangling IP takeovers
To effectively mitigate the risks associated with dangling IP takeovers, a holistic approach that integrates proactive measures with automated processes is a must. With this strategy, a strong defence can be created against dangling IP exploitation, enhancing the integrity and safety of cloud environments.
Best practices to mitigate dangling IP takeover risks
The following safeguards are fundamental components in the architecture of cloud security, serving as the first line of defence in the prevention of IP-related vulnerabilities.
DNS management and audits
Begin with rigorous DNS management by ensuring that DNS entries are removed before terminating a resource associated with an ephemeral IP or when releasing an elastic IP back to the pool. Complement this with regular audits and continuous monitoring of cloud resources. Employ automated tools capable of real-time visibility into cloud infrastructure changes, which are instrumental in identifying and remedying dangling IPs proactively.
Elastic IP lifecycle management
Develop and enforce comprehensive policies for the allocation, association, disassociation, and release of Elastic IPs (EIPs). These policies should dictate that EIPs be either immediately reassigned or released upon cessation of their need, thus closing the window of vulnerability that attackers could exploit.
Access control: Emphasising Service Control Policies (SCPs)
Within the realm of access control, leverage the power of Service Control Policies (SCPs) to enforce the principle of least privilege across your organisation’s cloud infrastructure. SCPs enable central control over permissions, allowing you to define and limit the actions that can be taken, thereby reducing the chance of unintended dangling EIPs. For instance, by implementing an SCP that denies the action ec2:EnableAddressTransfer, you prevent the unauthorised or accidental transfer of EIPs:
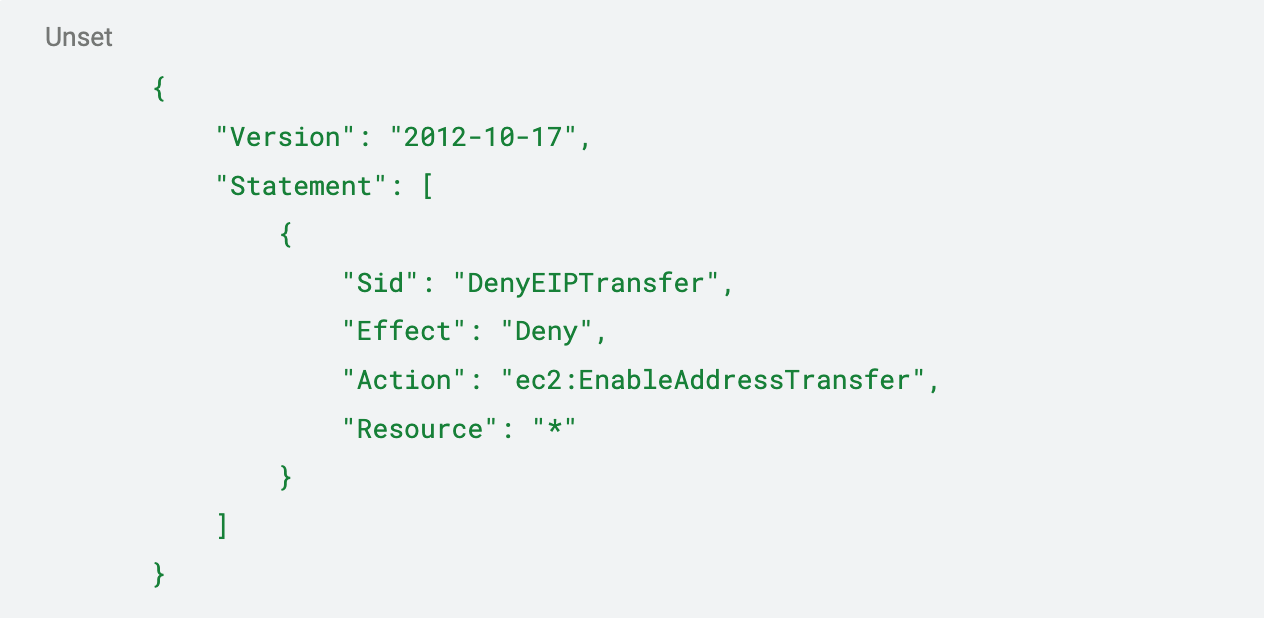
This policy snippet serves as a practical example of how SCPs can be a linchpin in your security strategy, ensuring that such critical operations are only performed under tightly controlled conditions. It is vital to highlight the significance of SCPs by making it a bold, standalone point within the access control section, demonstrating its weight in the overall security posture.
Education and awareness
Lastly, fortify your security framework by investing in education and awareness programs for your staff. They should be well-informed about the potential risks associated with dangling IPs and the best practices to avoid such threats. Comprehensive training will instil a culture of security mindfulness that complements the technical safeguards you have in place.
Strengthening security through automation
Automating the detection and management of dangling IPs can significantly enhance an organisation’s security posture. Automation provides immediate visibility into potential vulnerabilities, improves operational efficiency by eliminating manual checks, and enables swift responses to mitigate risks.
By understanding the risks associated with dangling IPs and implementing robust mitigation strategies, organisations can protect themselves from potential security breaches, ensuring the integrity and safety of their cloud environments.
Automated detection of dangling IPs
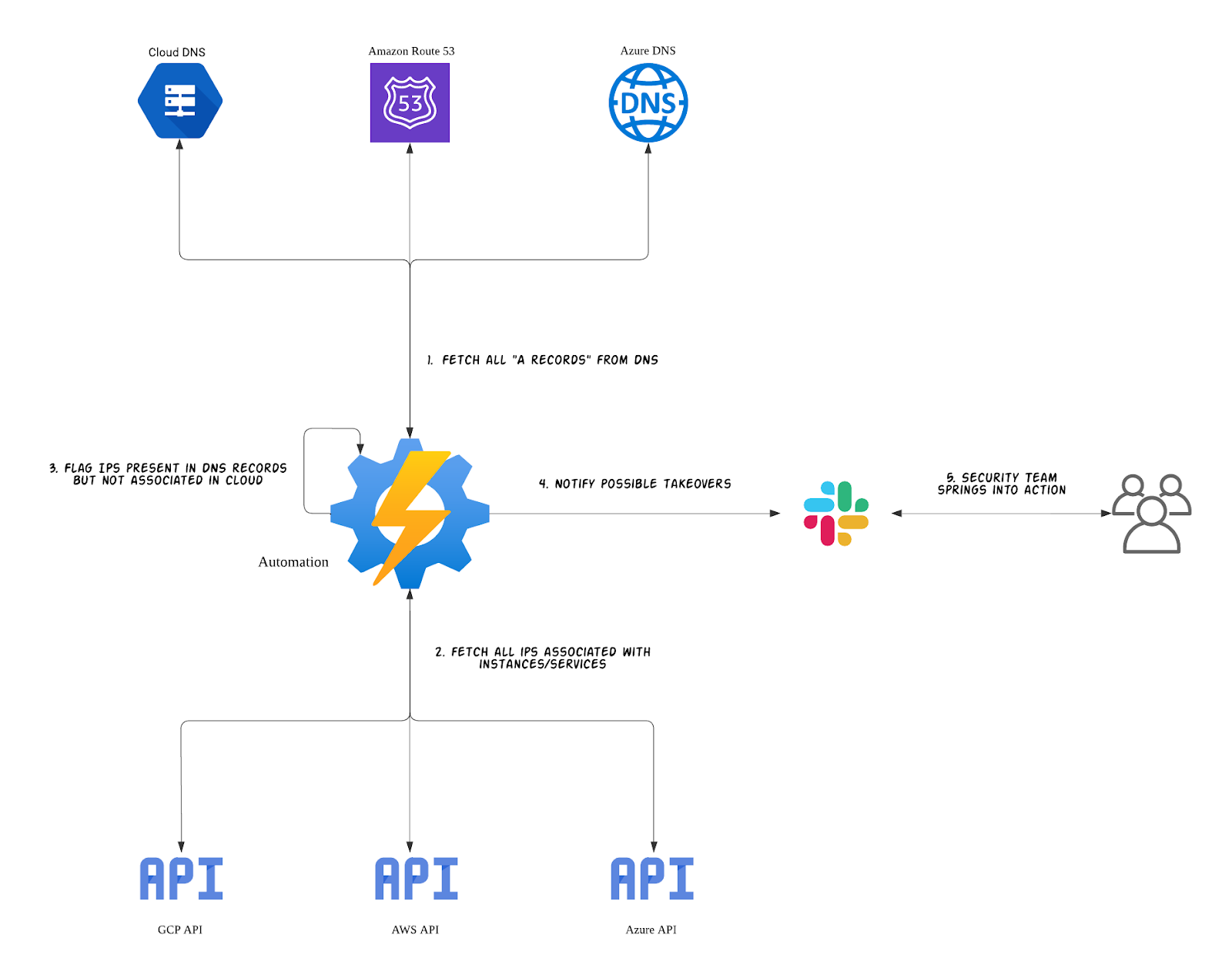
Here is how the automated process for detecting dangling IPs works:
- The tool retrieves all DNS A Records from your DNS providers. It then filters these records to identify those that correspond to the public IP ranges of your cloud service providers (e.g., AWS, GCP, or Azure).
- Simultaneously, it fetches all public IPs associated with resources across your cloud accounts. This includes instances, load balancers, and other relevant services.
- It then compares the IP addresses from the DNS records with those associated with actual cloud resources. Any IP that has an active DNS record but is not currently associated with a cloud resource is flagged as a potential risk for dangling IP takeover.
- Upon identifying potential dangling IPs, a notification is sent to the internal security team through a pre-defined communication channel, such as Slack. This prompt alerting enables swift action to address and secure any identified vulnerabilities.
By automating the detection of dangling IPs and streamlining the notification process, organisations can achieve several key benefits:
- Immediate visibility: Security teams gain immediate insights into potential vulnerabilities, reducing the attackers’ window of opportunity.
- Improved efficiency: Automating routine checks for dangling IPs frees up valuable resources, allowing security teams to focus on more strategic security initiatives.
- Prompt response: Streamlined communication through integration with messaging platforms like Slack facilitates rapid communication and coordination among security teams, enabling prompt remediation actions to mitigate risks.
Conclusion
Dangling IP takeovers pose a critical security threat in cloud computing, enabling attackers to intercept traffic, launch malicious activities, and access sensitive information. This vulnerability stems from poorly managed elastic and ephemeral IPs. To counter this threat, organisations must implement focused security measures: thorough DNS management, continuous cloud resource audits, strict elastic IP lifecycle policies, access control based on the least privilege principle, and comprehensive staff training. Automating the detection and management of dangling IPs enhances security by providing timely insights, increasing efficiency, and enabling quick risk mitigation. Effective strategies and automation are crucial for protecting against dangling IP exploits, thus securing the cloud infrastructure against potential breaches.
About the authors
Vishal Panchani is the Development Security Team Lead at Deriv. He is passionate about internet safety, especially when it comes to pen-testing and DevSecOps.
Ritik Karayat is a Product Security Engineer at Deriv, curious about how everything works under the hood. He loves to dive deep into computer technologies and explore their fundamental building blocks, such as OS/Kernel and their security implementations.
